gdx9902
12 years agoNew Contributor
Help needed for HTTPS handshake between SOAPUI and GSOAP lib
Hi I have been writing my own application which incorporates SSL support functionality on an embedded linux platform. I am having a lot of difficulty with the handshake process.
I am currently using the latest GSOAP library with the OPENSSL support. I am constantly bombarded with handshake errors, and cannot send data to and from SOAPUI and GSOAP, even though the context maybe alright.
I have followed the GSOAP coding examples and initialize the soap client context as required. The code is as follows below:
I used the scripts that was present in the GSOAP lib ssl sample to generate all the keys and certificates. the following is a breakdown of what I performed:
1) I created my own CA signing authority calling ./root.sh, the commands called were:
openssl req -newkey rsa:1024 -sha1 -keyout rootkey.pem -out rootreq.pem
openssl x509 -req -in rootreq.pem -sha1 -extfile openssl.cnf -extensions v3_ca -singkey rootkey.pem -out cacert.pem -days 1095
cat cacert.pem rootkey.pem >root.pem
openssl x509 -subject -issuer -dates -noout -in root.pem.
From my understanding, this created:
rootkey.pem -> my own CA key
rootreq.pem-> my own CA's request certificate
cacert.pem -> my own signed certificate using the rookey and rootreq.
root.pem -> the final certificate which is the cacert.pem and rootkey.pem concatinated together.
2) Generate my device's and soap ui's keys and certificates using openssl by calling the cert.sh script. The following commands were done:
openssl req -newkey rsa:1024 -sha1 -keyout scukey.pem -out scureq.pem
openssl req -newkey rsa:1024 -sha1 -keyout soapkey.pem -out soapreq.pem
openssl x509 -req -in scureq.pem -sha1 -extfile openssl.cnf -extensions usr_cert -CA root.pem -CAkey root.pem -CAcreateserial -out scucert.pem -days 1095
openssl x509 -req -in soapreq.pem -sha1 -extfile openssl.cnf -extensions usr_cert -CA root.pem -CAkey root.pem -CAcreateserial -out soapcert.pem -days 1095
cat scucert.pem scukey.pem cacert.pem > scu.pem
cat soap.pem soapkey.pem cacert.pem > soap.pem
openssl x509 -subject -issuer -dates -noout -in scu.pem
openssl x509 -subject -issuer -dates -noout -in soap.pem
From my understanding scu.pem is the certificate key for my device and soap.pem is my certificate/key for my SOAPUI. My device certificate is called from the code I have pasted above. the tricky part i thought was to convert the soap.pem and cacert.pem to the jks format for SOAPUI to use.
The commands I used to convert the two files were as follows:
1) For cacert.pem:
keytool -import -v -alias -trustcacerts mycacert -file cacert.pem -keystore cacert.jks -storepass password
This created a cacert.jks file which I used for the MOCK TRUSTSTORE.
2) For soap.pem
2a) I first converted the pem to pkcs12 format to preserve the certificate key chain
openssl pkcs12 -export -out soap.p12 -inkey soap.pem -in soap.pem -certfile soap.pem
2b) I then converted the soap.p12 file to jks format using keytools
keytool -importkeystore -srckeystore soap.p12 -destkeystore soap.jks -srcstoretype PKCS12 -deststoretype JKS
The password i typed was the same, "password"
2c) Then I import the cacert.jks into the newly formed soap.jks keystore.
keytool -import -keystore soap.jks -alias mycacert -file cacert.jks
I used the newly formed soap.jks as the keystore for both regular communications and soapui client authentication.
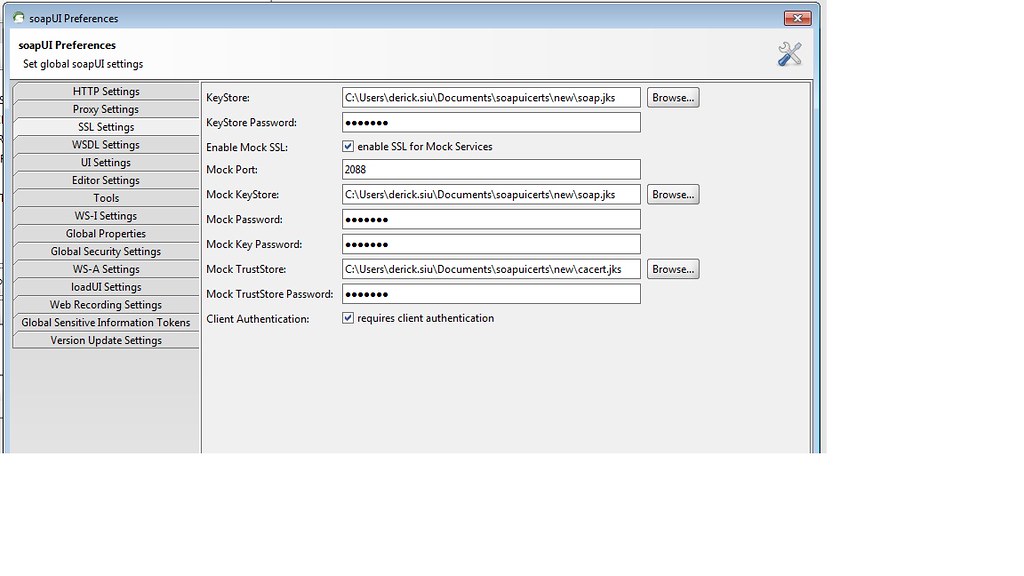
With all that said, my SOAPUI ssl set up is as follows:
once all that has been set up, i cannot get the handshake to work. I have even tried to create the keys using keytools and convert the certificates to pem files, and it still won't work.
The errors I am receiving from what I can see are:
1)
"SSL_ERROR_SSL
error:140770FC:SSL routines:SSL23_GET_SERVER_HELLO:unknown protocol"
Detail: SSL_connect error in tcp_connect()
This occurs everytime i try to send data from my device to SOAPUI ( my device acts as a client and SOAPUI acts as a SERVER)
2)"SSL/TLS error"
Detail: Can't setup context
Error 30 fault: SOAP-ENV:Server [no subcode]
"SSL/TLS error"
This occurs everytime i try to send data/commands to my device from SOAPUI (my device acts as a server and SOAPUI acts as a CLIENT)
I am not sure where I went wrong, and have been pounding my head on a brick wall for the past week. If anyone has anything that can help would be very much appreciated.
Thank you
I am currently using the latest GSOAP library with the OPENSSL support. I am constantly bombarded with handshake errors, and cannot send data to and from SOAPUI and GSOAP, even though the context maybe alright.
I have followed the GSOAP coding examples and initialize the soap client context as required. The code is as follows below:
if(type)
{
iError = soap_ssl_client_context(soap,
(SOAP_SSL_DEFAULT),
"scu.pem",
"password",
"cacert.pem",
CERTIFICATE_PATH,
NULL);
}
else{
iError = soap_ssl_server_context(soap,
SOAP_SSL_REQUIRE_CLIENT_AUTHENTICATION,
"scu.pem",
"password",
"cacert.pem",
CERTIFICATE_PATH,
NULL,
NULL,
NULL,
NULL);
}
I used the scripts that was present in the GSOAP lib ssl sample to generate all the keys and certificates. the following is a breakdown of what I performed:
1) I created my own CA signing authority calling ./root.sh, the commands called were:
openssl req -newkey rsa:1024 -sha1 -keyout rootkey.pem -out rootreq.pem
openssl x509 -req -in rootreq.pem -sha1 -extfile openssl.cnf -extensions v3_ca -singkey rootkey.pem -out cacert.pem -days 1095
cat cacert.pem rootkey.pem >root.pem
openssl x509 -subject -issuer -dates -noout -in root.pem.
From my understanding, this created:
rootkey.pem -> my own CA key
rootreq.pem-> my own CA's request certificate
cacert.pem -> my own signed certificate using the rookey and rootreq.
root.pem -> the final certificate which is the cacert.pem and rootkey.pem concatinated together.
2) Generate my device's and soap ui's keys and certificates using openssl by calling the cert.sh script. The following commands were done:
openssl req -newkey rsa:1024 -sha1 -keyout scukey.pem -out scureq.pem
openssl req -newkey rsa:1024 -sha1 -keyout soapkey.pem -out soapreq.pem
openssl x509 -req -in scureq.pem -sha1 -extfile openssl.cnf -extensions usr_cert -CA root.pem -CAkey root.pem -CAcreateserial -out scucert.pem -days 1095
openssl x509 -req -in soapreq.pem -sha1 -extfile openssl.cnf -extensions usr_cert -CA root.pem -CAkey root.pem -CAcreateserial -out soapcert.pem -days 1095
cat scucert.pem scukey.pem cacert.pem > scu.pem
cat soap.pem soapkey.pem cacert.pem > soap.pem
openssl x509 -subject -issuer -dates -noout -in scu.pem
openssl x509 -subject -issuer -dates -noout -in soap.pem
From my understanding scu.pem is the certificate key for my device and soap.pem is my certificate/key for my SOAPUI. My device certificate is called from the code I have pasted above. the tricky part i thought was to convert the soap.pem and cacert.pem to the jks format for SOAPUI to use.
The commands I used to convert the two files were as follows:
1) For cacert.pem:
keytool -import -v -alias -trustcacerts mycacert -file cacert.pem -keystore cacert.jks -storepass password
This created a cacert.jks file which I used for the MOCK TRUSTSTORE.
2) For soap.pem
2a) I first converted the pem to pkcs12 format to preserve the certificate key chain
openssl pkcs12 -export -out soap.p12 -inkey soap.pem -in soap.pem -certfile soap.pem
2b) I then converted the soap.p12 file to jks format using keytools
keytool -importkeystore -srckeystore soap.p12 -destkeystore soap.jks -srcstoretype PKCS12 -deststoretype JKS
The password i typed was the same, "password"
2c) Then I import the cacert.jks into the newly formed soap.jks keystore.
keytool -import -keystore soap.jks -alias mycacert -file cacert.jks
I used the newly formed soap.jks as the keystore for both regular communications and soapui client authentication.
With all that said, my SOAPUI ssl set up is as follows:

once all that has been set up, i cannot get the handshake to work. I have even tried to create the keys using keytools and convert the certificates to pem files, and it still won't work.
The errors I am receiving from what I can see are:
1)
"SSL_ERROR_SSL
error:140770FC:SSL routines:SSL23_GET_SERVER_HELLO:unknown protocol"
Detail: SSL_connect error in tcp_connect()
This occurs everytime i try to send data from my device to SOAPUI ( my device acts as a client and SOAPUI acts as a SERVER)
2)"SSL/TLS error"
Detail: Can't setup context
Error 30 fault: SOAP-ENV:Server [no subcode]
"SSL/TLS error"
This occurs everytime i try to send data/commands to my device from SOAPUI (my device acts as a server and SOAPUI acts as a CLIENT)
I am not sure where I went wrong, and have been pounding my head on a brick wall for the past week. If anyone has anything that can help would be very much appreciated.
Thank you
- Hi Derick,
This forum is dedicated to TestComplete, another tool by SmartBear.
While TestComplete and SoapUI are the products of the same company, I think that you'd better to post your question here: http://forum.soapui.org/index.php.